Cyber Attack on Energy Supplier People's Energy compromises an entire database
Scotland based Energy supplier People's Energy has been hacked, resulting in the company informing all 270,000 of its customers that their data may have been compromised.
What happened?
The company revealed that it had discovered the attack on Wednesday and immediately set about securing its systems. However, it seems they were unable to act fast enough as the hackers were able to steal the personal details of hundreds of thousands of their current and former customers.
"On Wednesday 16 December, we discovered that an unauthorised third party had gained access to one of the systems we use to store some of our members' data. As soon as we became aware of what was happening, we acted immediately to close down the route being used to get into our system, and to stop access to any further information.
Details for all our members were accessed. This includes both current members and former members who've used us as their energy supplier in the past. We're doing everything we can to contact everyone affected to explain what's happened. We've informed the Information Commissioner's Office and the energy industry regulator, Ofgem. We're following their guidance, and are keeping them updated on the situation,"
People's Energy said in an email sent to customers.
According to the company, 15 of its small business customers had their financial details compromised, but the rest of their customers' financial data was secure. The bulk of the data stolen included dates of birth, addresses, phone numbers, names, tariff information and energy meter IDs.
"This is a big blow in every way. We want people to feel they can trust us. This was not part of the plan. We're upset and sorry," said People's Energy Co-founder Karen Sode.
Also read: Elexon hit by Cyber Attack
Customers warned to be on alert
A cyber attack can prove devastating to any company, but it is the customers who are now likely to face increased threats.
With the data stolen they are likely to be targeted for phishing scams (where a criminal uses the stolen data to pose as someone else to dupe their target out of sensitive information or money) and other attempts to defraud them.
Cyber attacks are particularly damaging to energy suppliers due to the impact they have on a company's reputation.
If a company cannot be trusted to safeguard its customers' sensitive information, then why would a consumer stick with them? The worst thing a company can do is try and cover up such incidents.
People's Energy did a good job of quickly reacting and informing their customers, but questions will be raised as to how such an attack was able to be carried in the first place.
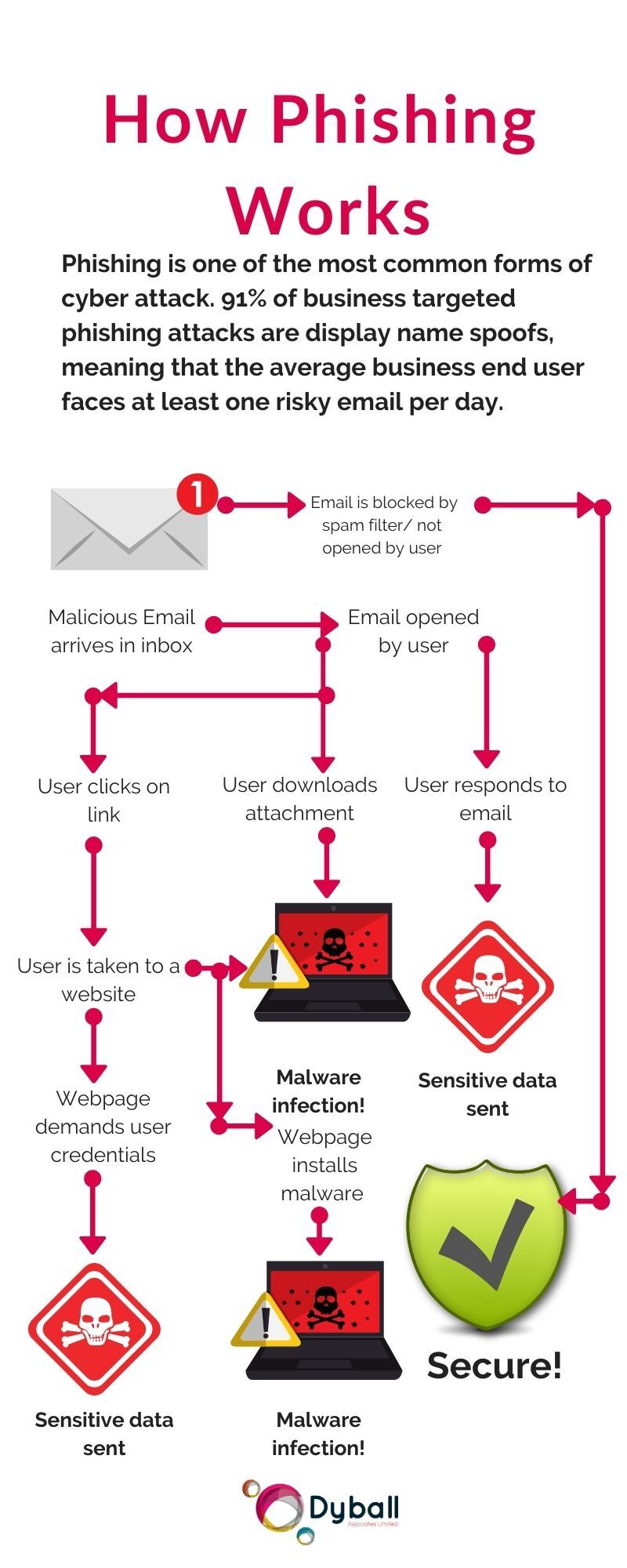
How to spot Phishing attacks
Phishing attacks may be the most common form of cyber-attack, but that doesn't mean that you're helpless in the face of the threat.
There are a few methods you can use to spot them but bear in mind that phishing attacks come in a wide variety of forms with some being far more sophisticated than others.
Sometimes a phishing email will claim to be from an organisation and use logos to appear more professional. Is the design quality what you would expect from the sender? Check the email headers or flag into your internal IT department. Phishing emails can easily spoof email addresses to make them seem legitimate.
If an email is not addressed to you by name, then it could be a sign that the sender doesn't know you and is merely hoping to get lucky. If it is addressed to you directly but looks suspicious, then you may be the target of a Spear Phishing campaign.
You should instantly be suspicious of any emails making demands or threats. Never give out your details.
Anti-spoofing mitigations such as The Domain-based Message Authentication, Reporting and Conformance (DMARC) email standard can be used to protect against spoofing.
Be aware of emails that may come from someone high up in your organisation requesting the transfer or payment of funds to a specific bank account. If being responsible for handling money isn't your job, then report it immediately.
Does the email appear legitimate, or is it trying to mimic someone you know? A hacker can ascertain your connections via social media profiles, so make sure to check your privacy settings.
If something appears too good to be true, then it is. If someone claims to be offering you money or a prize over the internet then run for the hills, chances are they are a scammer. Remember, there is no such thing as a free lunch.
Check the email address
If you receive an unsolicited email claiming to be from a company the easiest way to check whether it's legit is to search for the company online. If searching the name of the sender leads you to a shoddy looking website or comes up with nothing, then you can assume a scammer has sent the email. If the domain name (the bit after the @ symbol in the sender's email address) matches the apparent sender of the email, the message is probably legitimate.
Check for spelling and grammatical errors
As many phishing emails are sent from overseas, they often contain spelling mistakes, poor punctuation and grammar. Sometimes a scammer will deliberately include these to see if you will respond regardless. If you do, then you will be marked as an easy target for future scams.
The email is poorly written
This follows on from the point above in that many phishing scammers operate overseas. Often a phishing email is worded poorly, or the sentence structure doesn't make much sense.
Don't click that link
Often the objective of phishing scams is to trick you into clicking on a malicious link or download a harmful file. Often these links contain malware that then goes on to infect your device. The particularly harmful strain of malware called ransomware often spreads this way. Always bear in mind that if something appears too good to be true, then it probably is.
The message creates a sense of urgency
Another favourite tactic used by scammers is to create a sense of urgency around the messages they're sending. Hackers have learned to prey on people's concerns, often using the words' important' or 'urgent' in the messages they send. If you receive such emails, then it's natural to want to know what the message contains. A favourite strategy often used against businesses is for the hacker to pose as the human resources or finance department.
Energy Suppliers at high cyber-attack risk
Energy suppliers are a highly tempting target for cybercriminals due to the large amount of data they process and store.
A report released by Hiscox in October showed that energy supply companies top the list when it comes to the businesses most at risk from cyber-attack.
According to the report, the energy sector experienced median losses of over £100,000 within the last year and topped the table for the sectors most at risk.
Also read: Energy Supply companies most vulnerable to cyber-attack says new report
One challenge People's Energy is facing and indeed one that most companies that have suffered a breach face is communicating with their customers.
With news of the breach, customers are to be very suspicious of any emails coming from the company, so they now have the challenge of convincing their customers that their emails are indeed legitimate. One way around this is to post a notice on the company website or send the message via the post.
Energy suppliers should be on heightened alert over the festive period as cyber criminals typically take advantage of the distractions created by the holiday season.
Further Reading
Dyball Associates Achieves ISO27001 Certification
Dyball Associates are proud to help new supply businesses successfully launch in the UK market.
Through our energy market consultancy services, and the software we've developed, we're supporting new UK electricity and gas suppliers get set up and start supplying.
For more information on how to start and manage an energy company, get in touch with Dyball Associates today.